Pegasus: How to check for spyware on your phone

Am I on the list of phone numbers targeted by NSO Group's Pegasus spyware?
That is the question thousands of journalists, activists and officials have been asking since an investigation led by Forbidden Stories and Amnesty International revealed 50,000 phone numbers of targets have been identified in a data leak.
Naturally, the groups involved in the investigation are inundated with requests for their numbers to be checked on the list and their phones to be assessed.
So far, a few hundred people have been identified. They include French President Emmanuel Macron and Morocco’s King Mohammed VI – both of whom were targeted by the Moroccan security services, according to the investigation.
Joining other officials like Iraqi President Barham Salih and Pakistani Prime Minister Imran Khan are journalists from outlets around the world, Azerbaijani and Hungarian dissidents, and close contacts of Jamal Khashoggi. NSO denies the allegations.
New MEE newsletter: Jerusalem Dispatch
Sign up to get the latest insights and analysis on Israel-Palestine, alongside Turkey Unpacked and other MEE newsletters
If you think you may be on the list and want to ask Amnesty and Forbidden Stories to check your number, don’t expect a response anytime soon, as hundreds of others are doing the same.
Can I search for Pegasus on my phone myself?
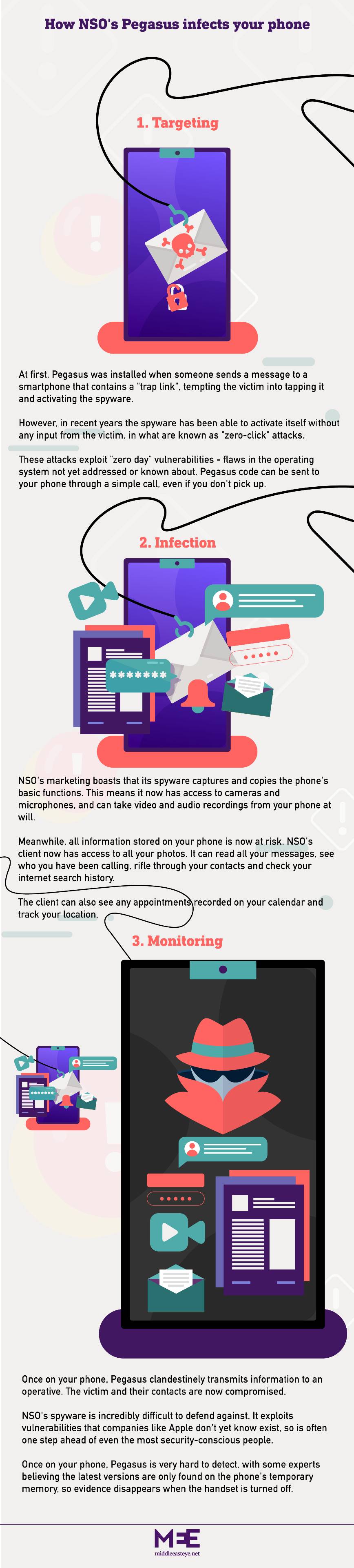
NSO’s latest Pegasus spyware is incredibly sophisticated. It targets vulnerabilities in the operating system of your phone that even its makers don’t yet know exist.
Meanwhile, some experts believe that the most recent versions are only found on the phone's temporary memory, so evidence disappears when the handset is turned off.
However, Amnesty Tech has released a toolkit to help people search their own phones for evidence of Pegasus.
The Mobile Verification Toolkit (MVT) can be used on Apple’s iOS and Android, using a device backup and searching for any indications that the spyware has been sent to your phone.
According to Amnesty it’s a bit easier to find it on iPhones than Androids, but indications should still be found nonetheless.
The MVT makes a backup of your entire phone, then rifles through looking for indicators of compromise that Amnesty knows are used by NSO. This could include domain names the company uses when it sends Pegasus through a message or call, for example.
Beware: For those not used to working toolkits like this, it can take some getting used to. Before using the MVT, you’ll need to use the open-source software package, Homebrew, to install libusb - a data transfer library - and the Python 3 programming language. The MVT page explains how.
Once up and running, the MVT will identify any files that indicate Pegasus has been rooting around your phone.
Rasha Abdul-Rahim, director of Amnesty Tech, warned that the toolkit is not suitable for use by novices, but the team is working to make it more user-friendly.
"This tool has been released as a forensic tool for a technical audience. Using it requires some technical skills such as understanding the basics of forensic analysis and using command line tools," she tweeted.
Middle East Eye delivers independent and unrivalled coverage and analysis of the Middle East, North Africa and beyond. To learn more about republishing this content and the associated fees, please fill out this form. More about MEE can be found here.