The 'significant expansion' of Israeli spyware use in the Gulf and beyond

A recent report showed that spyware produced by an Israeli-based cyber-warfare vendor, which only deals with governments, has witnessed “significant expansions” of usage in Saudi Arabia, the United Arab Emirates and Bahrain.
Citizen Lab, a research and development organisation at the University of Toronto, said on Tuesday that it tracked the use of Pegasus, a mobile phone spyware suite produced by Tel Aviv-based NSO Group between August 2016 and August 2018.
“Our findings paint a bleak picture of the human rights risks of NSO’s global proliferation. At least six countries with significant Pegasus operations have previously been linked to abusive use of spyware to target civil society,” said the report, naming the three Gulf Cooperation Council (GCC) countries, as well as Morocco.
Our findings paint a bleak picture of the human rights risks of NSO’s global proliferation. At least six countries with significant Pegasus operations have previously been linked to abusive use of spyware to target civil society
- Citizen Lab
NSO Group, which says it sells its products to "legitimate government agencies for the sole purpose of investigating and preventing crime and terror", came into the spotlight in recent years after reports emerged of governments using its Pegasus tool to spy on private individuals in Saudi, UAE and Mexico.
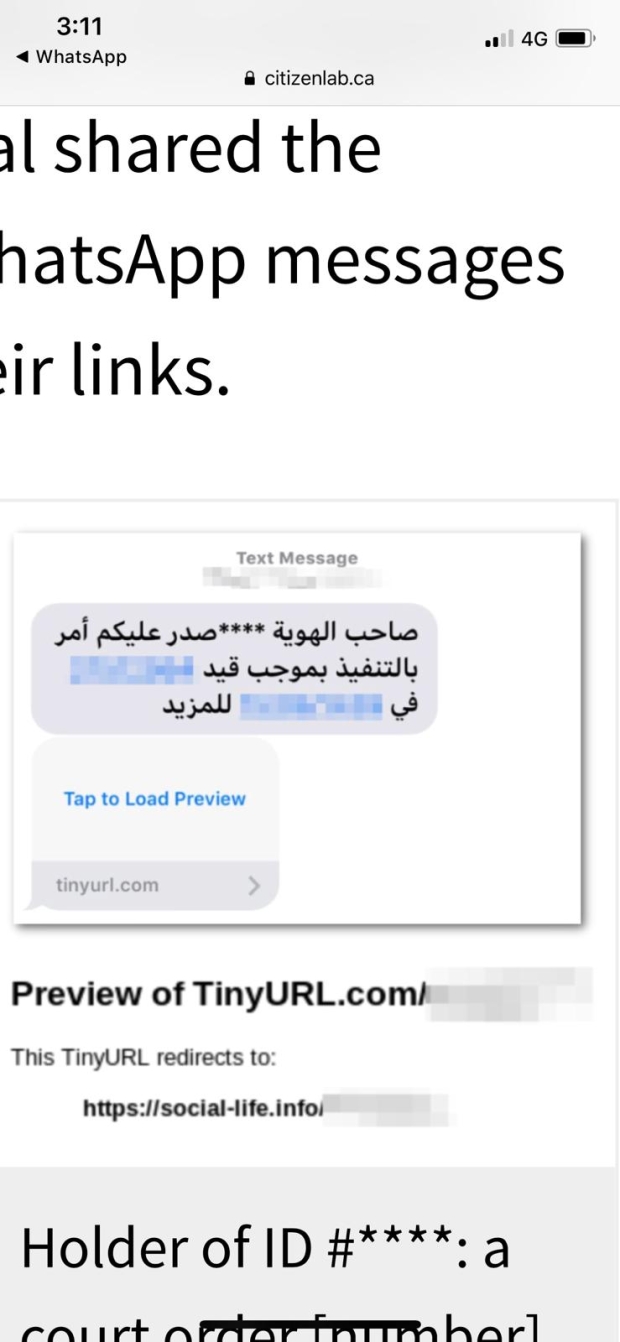
Amnesty International said in August that a staffer received a message via WhatsApp from a number they didn’t recognize about a protest supposedly taking place at the Saudi embassy in Washington, DC.
“When Amnesty’s tech team analysed the message, we found that clicking the link would have installed highly potent spyware - the Saudi protest was just carefully chosen bait,” said the international human rights watchdog, adding that a closer look into the domain name tied it to a “secretive company: NSO Group”.
Citizen Lab said that a similar method of baiting was used in Bahrain, where “politically themed domain names including shia-voice.com” were used. Bahrain’s government has been clamping down on the Shia majority demanding more political and social freedoms.
Middle East Eye's requests to Saudi Arabia, UAE and Bahrain for comments on the report were unanswered.
A recurring theme
The report comes weeks after the New York Times said that NSO is facing two lawsuits accusing it of actively participating in illegal spying.
The lawsuits, filed by a Qatari citizen and by Mexican journalists and activists, were filed in Israel and Cyprus, the newspaper said, and documents submitted with the lawsuits show that the UAE's rulers have been using the spyware Pegasus for at least a year.
According to the NYT, the Emiratis have tapped the phones of the Qatari emir, a chief editor of a London-based newspaper and a powerful Saudi prince. The UAE, along with Bahrain and Saudi Arabia, are in a row with Qatar that has seen the trio impose a land and sea blockade on their neighbour.
Citizen Lab said in its report that it identified at least six operators “with significant GCC operations, including at least two that appear to predominantly focus on the UAE, one that appears to predominantly focus on Bahrain, and one with a Saudi focus. Three operators may be conducting surveillance beyond the MENA region, including in Canada, France, Greece, the United Kingdom, and the United States.”
In response to questions, Bill Marczak, who led the reseach, said: "We can't conclusively say whether those governments use Pegasus based on our scanning results. What our scanning results do show us, however, is [there are] at least two operators that are operating only in the United Arab Emirates, and one operator that is operating primarily in Bahrain.
My speculation would be that those operators are the governments there. We also know that there is an operator that is operating in Saudi Arabia's interests
- Bill Marczak, Citizen Lab
"My speculation would be that those operators are the governments there. We also know that there is an operator that is operating in Saudi Arabia's interests, from our prior report with Amnesty."
The target of the spyware mentioned in Citizen Lab's joint report with Amnesty, Saudi national Yehia Assiri, told MEE "governments that use these technologies have something to be scared of, and have no respect for human rights.”
Assiri, a former air force officer who heads the rights advocate group ALQST, said in a phone interview from London that it’s also a reflection of these governments’ lies.
“They publicly claim their animosity towards Israel, but secretly use its products to spy on activists whom it then accuses of treason,” he said. Assiri said there was an attempt to bug his personal electronic devices, but both his mobile phone and computer crashed as a result of NSO’s Pegasus spyware.
Marczak added: "One interesting thing we identified is that at least five of the Middle East operators are spying on some targets in Qatar."
“The cases identified in this report raise serious doubts as to the depth and seriousness of NSO’s due diligence and concern for human rights protections. They also suggest that the company has a significant number of customers that maintain active infections in other countries, likely violating those countries laws,” said the report.
Marcazk said the best potential targets of the spyware should "keep an eye out for SMS or WhatsApp messages that look suspicious" and contact Citizen Lab.
In response to Citizen Lab’s report, NSO issued a statement saying there are multiple problems with the findings, including that “the list of countries NSO is alleged to operate in is simply inaccurate. NSO does not operate in many of the countries listed.”
Citizen Lab said the company’s response shows a misunderstanding of the report’s findings, and that “the list in our report is of suspected locations of NSO infections” and “not a list of suspected NSO customers”.
“The expanding user base of spyware like Pegasus will enable a growing number of authoritarian states to pry into the digital lives of their own citizens, but also into phones and computers in pockets and purses around the globe,” the report said.
This article is available in French on Middle East Eye French edition.
Middle East Eye propose une couverture et une analyse indépendantes et incomparables du Moyen-Orient, de l’Afrique du Nord et d’autres régions du monde. Pour en savoir plus sur la reprise de ce contenu et les frais qui s’appliquent, veuillez remplir ce formulaire [en anglais]. Pour en savoir plus sur MEE, cliquez ici [en anglais].